How to Secure Your Web Applications Using Modern Frameworks
In the rapid-fire world of AI development, where model accuracy and training speed often take center stage, security can sometimes feel like an afterthought. But as we transition from experimental notebooks to deploying scalable AI solutions in production, the attack surface expands significantly.
Modern web frameworks whether you’re using Django or FastAPI for your Python backends, or Next.js for your frontend come equipped with robust security features. However, simply using these frameworks isn’t a silver bullet. You need to know how to configure them correctly to protect your proprietary algorithms and sensitive training data.
In this article, you’ll learn:
- The specific security risks facing modern AI driven web applications.
- How to leverage built-in security features in frameworks like FastAPI, Django, and Flask.
- Best practices for authentication and authorization in microservices architectures.
- Strategies for securing API endpoints that serve machine learning models.
The Unique Security Landscape of AI Applications
Securing a standard CRUD (Create, Read, Update, Delete) application is a well-documented process. However, AI applications introduce unique vulnerabilities. When you are serving a TensorFlow or PyTorch model via an API, you aren’t just protecting user data; you are protecting high value intellectual property and potentially massive datasets.
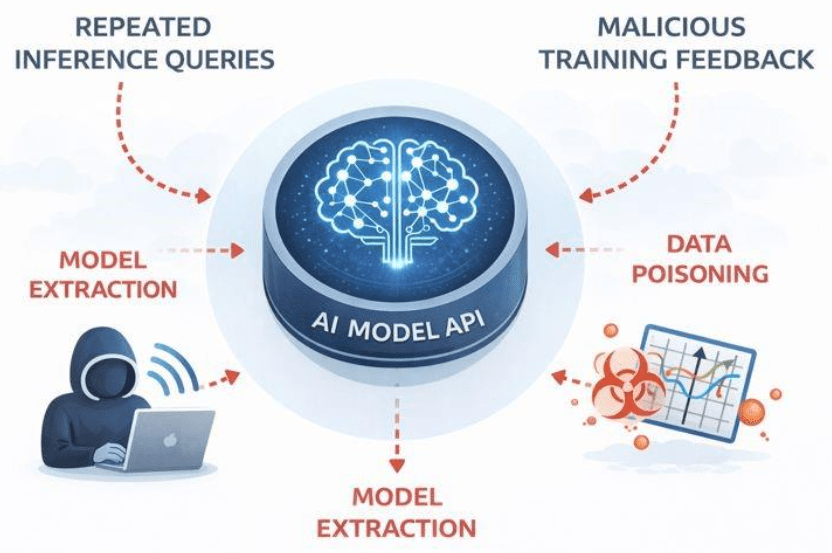
Model Inversion and Extraction
Attackers can sometimes query your API repeatedly to reconstruct the underlying model or extract the data it was trained on. This is known as model inversion or extraction. Standard web application firewalls (WAFs) might not detect these patterns because the requests look legitimate.
Data Poisoning
If your application accepts user feedback to retrain models (active learning), there is a risk of data poisoning. Malicious actors could inject bad data to skew the model’s predictions.
To mitigate these risks, we need to look at security not just at the model level, but at the web framework level that wraps your model.
Leveraging Framework Specific Security Features
Most data scientists and AI engineers prefer Python based frameworks due to their seamless integration with libraries like NumPy and Scikit learn. Let’s examine how to secure the three most popular options: FastAPI, Django, and Flask.
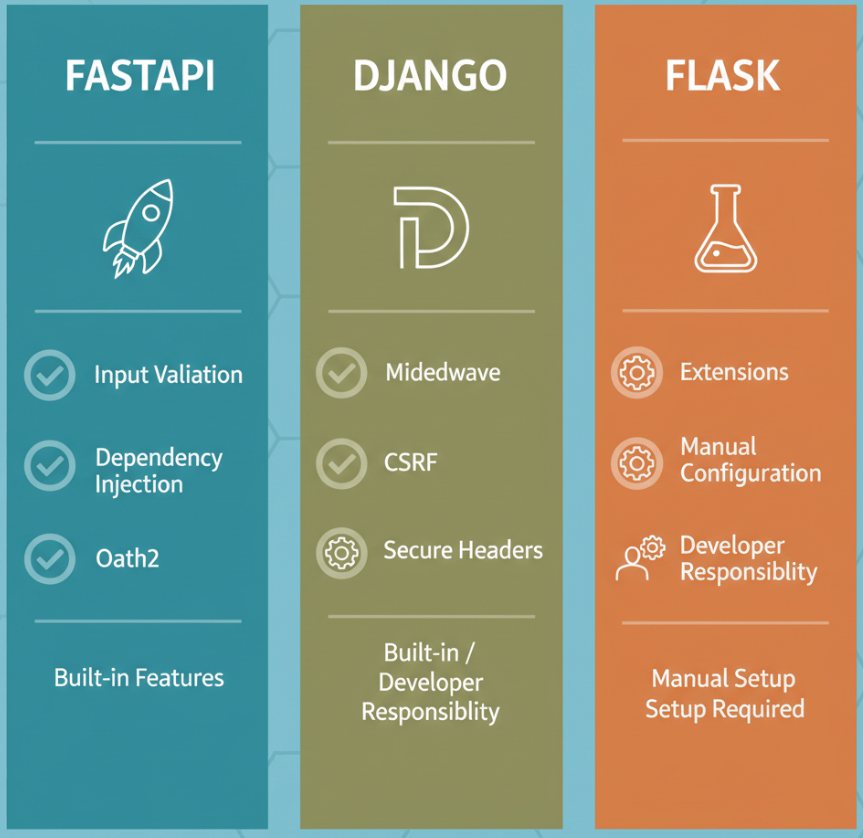
1. Securing FastAPI for High Performance Inference
FastAPI has become the go to choose for serving ML models because of its speed and native support for asynchronous programming. It creates a seamless tool for integration with real-time data processing.
Input Validation with Pydantic:
FastAPI uses Pydantic for data validation. This is your first line of defense. By strictly defining the schema of the input data your model expects, you prevent malformed data from causing exceptions or buffer overflows.
from fastapi import FastAPI
from pydantic import BaseModel, constr
app = FastAPI()
class PredictionInput(BaseModel):
# Enforce strict length and type checks to prevent injection attacks
text: constr(min_length=1, max_length=1000)
confidence_threshold: float
@app.post(“/predict”)
async def predict(input_data: PredictionInput):
# Logic to call your model
return {“result”: “prediction”}
Dependency Injection for Security:
FastAPI’s dependency injection system allows you to create reusable security dependencies. You can easily implement OAuth2 with Password (and hashing), ensuring that every endpoint request is authenticated before it even touches your model inference logic.
2. Django: The “Batteries Included” Approach
If your AI application requires a full featured backend with user management, Django is often the preferred choice. It handles SQL injection, cross site scripting (XSS), and cross site request forgery (CSRF) out of the box.
Middleware Configuration:
Ensure your settings.py middleware is correctly ordered. The SecurityMiddleware should be near the top.
MIDDLEWARE = [
‘django.middleware.security.SecurityMiddleware’,
‘django.contrib.sessions.middleware.SessionMiddleware’,
‘django.middleware.common.CommonMiddleware’,
‘django.middleware.csrf.CsrfViewMiddleware’,
# … other middleware
]
Secure Headers:
Django allows you to easily set HTTP Strict Transport Security (HSTS), X Content Type Options, and X Frame Options. For enterprise grade applications in finance or healthcare, enabling HSTS is non-negotiable to prevent man in the middle attacks.
3. Flask: Flexibility Requires Vigilance
Flask is lightweight, making it excellent for microservices, but it leaves many security decisions up to the developer.
Secure Cookies:
If you are using sessions, you must set SESSION_COOKIE_SECURE = True and SESSION_COOKIE_HTTPONLY = True. This ensures cookies are only sent over HTTPS and cannot be accessed via JavaScript, mitigating XSS attacks.
Rate Limiting:
Since ML inference is computationally expensive, a Denial Service (DoS) attack can easily overwhelm your GPU resources. Integrating a library like Flask Limiter is essential to boost your AI capabilities without risking downtime.
Authentication and Authorization in Microservices
In a modern MLOps architecture, your model likely sits as a microservice containerized in Docker, communicating with other services. Trusting internal traffic is a common mistake.
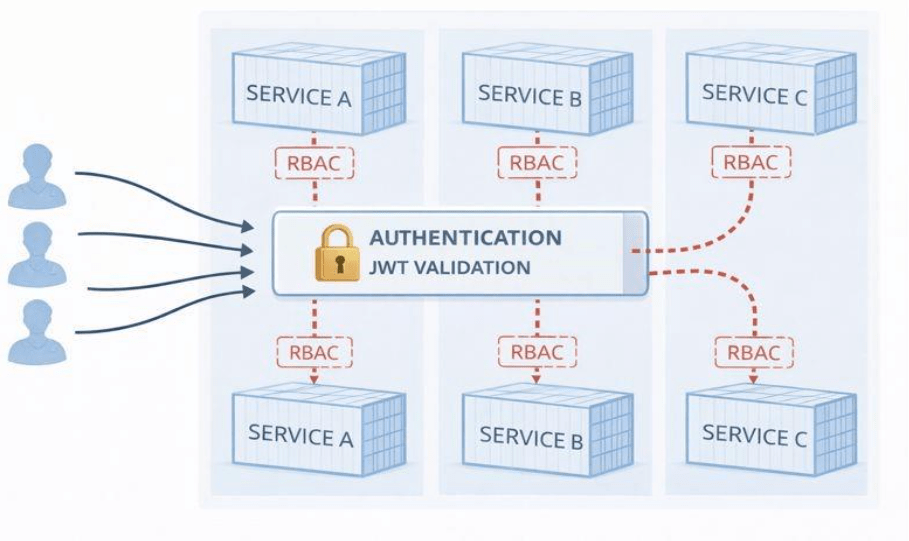
Implement Zero Trust Architecture
Adopting a Zero Trust approach means verifying every request, even those coming from inside your network.
- JSON Web Tokens (JWT): Use JWTs for stateless authentication between services. Ensure tokens are signed using a strong algorithm (like RS256) and have short expiration times.
- Role Based Access Control (RBAC): Not every service needs full access. A data processing service might need to write access to your S3 bucket, but your inference service only needs to read access.
Managing Secrets
Never hardcode API keys or database credentials in your code. Use environment variables or secrets management tools like HashiCorp Vault or AWS Secrets Manager. When deploying scalable AI solutions using Kubernetes, utilizing Kubernetes Secrets ensures that sensitive information is encrypted at rest.
Securing the Deployment Pipeline (CI/CD)
Security doesn’t start when the application is deployed; it starts in the pipeline.
Static Application Security Testing (SAST):
Integrate SAST tools into your CI/CD pipeline. Tools like Bandit (for Python) can scan your codebase for common security issues, such as hardcoded passwords or unsafe uses of eval().
Container Scanning:
Before your Docker container is pushed to the registry, scan it for vulnerabilities. Base images (like python:3.9 slim) often have known vulnerabilities that need patching. Tools like Trivy or Clair can automate this process.
Conclusion: Security as an Enabler, not a Blocker
Securing web applications that host AI models is critical for maintaining performance, protecting intellectual property, and ensuring regulatory compliance in industries like healthcare and finance. By leveraging the built-in features of modern frameworks and adopting a security first mindset in your architecture, you can deploy scalable solutions with confidence.
Don’t wait for a breach to prioritize security. Audit your current frameworks today, implement strict input validation, and ensure your authentication protocols are robust.
Leave a comment